Hacken Analysis: A comprehensive Hacken review and outlook of the upcoming Hacken ICO, which is set to revolutionize and disrupt the cybersecurity market.
This represents the writer’s personal opinions and does not – in any way- constitute a recommendation of an investment or financial advice. Please assume caution when investing in cryptocurrencies and do so at your own risk, as it is extremely volatile and you can lose your money.
Overview
Hacken is a community-powered cybersecurity ecosystem for white-hat hacking (or ethical hacking). White hat hackers are expert, ethical hackers that specialize in testing and enhancing the security of an entity’s IT system, through exposing certain flaws or vulnerabilities inherent within the system. The core component of the Hacken ecosystem – the Hacken marketplace – features a platform which connects ethical hackers with developers that require fixes and enhancement of their systems.
Features of Hacken Ecosystem
 There are 5 components that make up the Hacken ecosystem, which includes:
There are 5 components that make up the Hacken ecosystem, which includes:
- The HackenProof Marketplace: A bug bounty marketplace where anyone can send their code to be evaluated for bugs and vulnerabilities by white hat hackers
- The Unreported Zero-Day Remuneration Platform: A transparent fund focused on financially rewarding an unknown computer software vulnerability, ensuring that it doesn’t fall into the wrong hands
- A Cybersecurity Analytics Center: A research and analytics platform that will act as a supporting function within the ecosystem. The research would also be available via subscription or direct acquisition basis
- The Hacken Accelerator: An incubator that will foster the creation of start-ups within the Hacken ecosystem
- The HackIT Conference: An annual, community-driven, international cybersecurity forum which also features 3 competitions for global participants. It’s a great platform to identify and develop talents
Applications
What’s interesting behind the concept of Hacken, is that it creates a dedicated cybersecurity platform that allows white hat hackers to solve the needs of those requiring security fixes and enhancements. This is a big step towards formalizing the notion of ethical hacking and Hacken could very well be at the forefront of its advancement. Hacken utilizes the Blockchain in 2 ways:
- Proof of Vulnerability Testing: Hacken utilizes a sidechain to record all relevant data about the product, the terms of service agreement and a timestamp. The next block will contain data on the vulnerabilities discovered during the bug bounty program as well as the fixes. The hashes of these blocks will be then recorded on the Ethereum blockchain where it will be immutable. All completed programs will receive a Hacken security certificate, which acts as a seal of credibility that the software has been tested by Hacken. (Read more: What’s the Difference Between Ethereum and Ethereum Classic?)
- Smart contracts will be utilised on 2 fronts;
- Hacken will keep 80% of the funds raised in token sale in a multi-signature escrow account, which will be annually audited via the Public Board of Trustees of the Hacken Ecosystem
- Every transaction on the HackenProof marketplace will be executed using an escrow powered by smart contracts. A simple way to illustrate this is when clients set the parameters and bounty payment for their programs, they will send the payment to a smart contract which will only be executed (paid to the white hat hackers) if the deliverables are achieved
Token Analysis
Rationale for Tokens
There are 2 main rationales apparent when analysing Hacken, which are:
Value Independence: Hacken tokens (HKN) represents the currency mode within the Hacken ecosystem; anyone who requires cybersecurity services within the ecosystem needs to have HKN tokens. This means that the value of HKN is determined freely by the market, independent from the volatility of other currencies
Store of Value: HKN represents a deflationary currency (currency with decreasing supply) due to its burning mechanism. This means that its value would theoretically appreciate, thereby increasing its utility as a store of value.
Token Breakdown
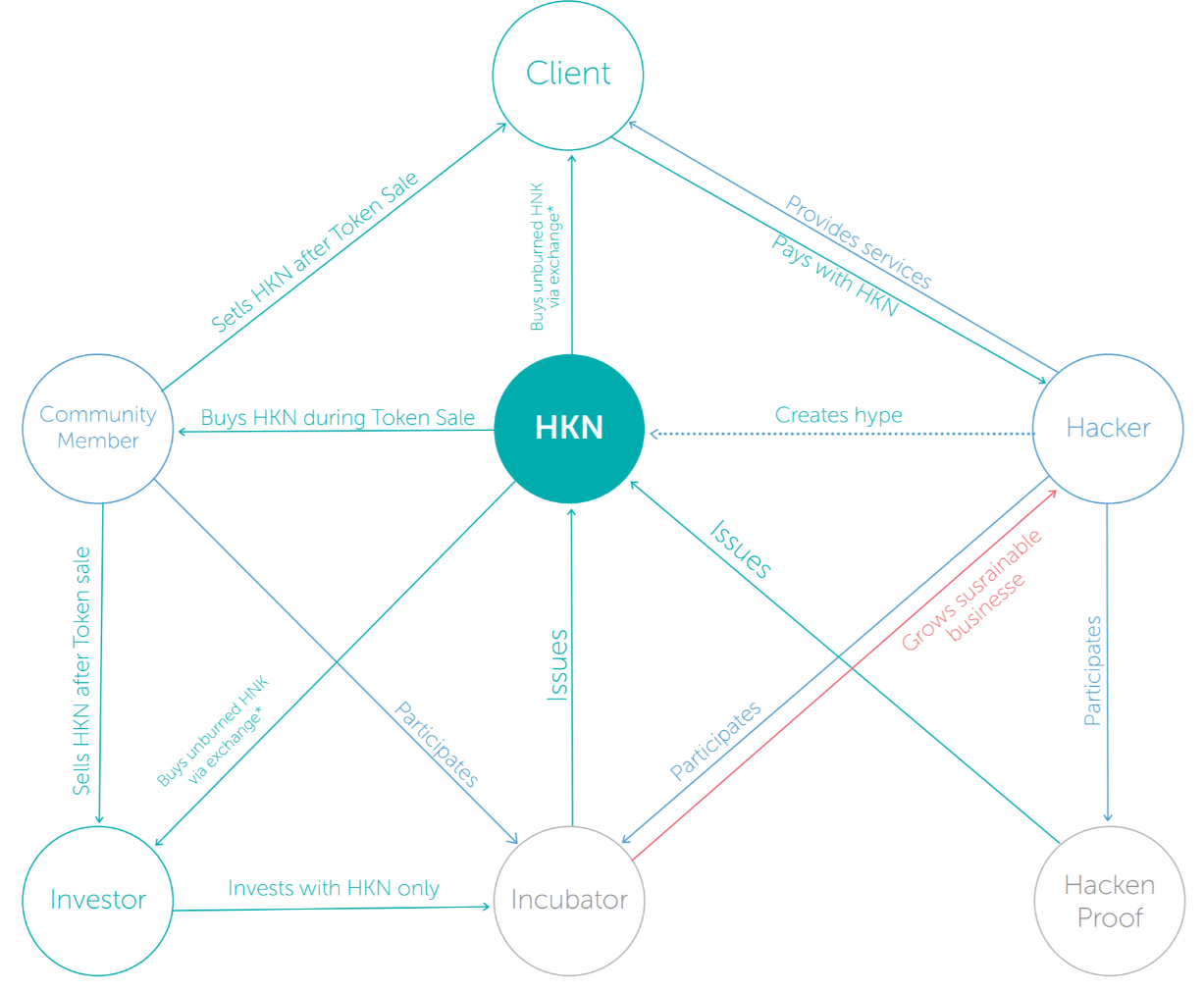
Here is the breakdown of the HKN ICO: 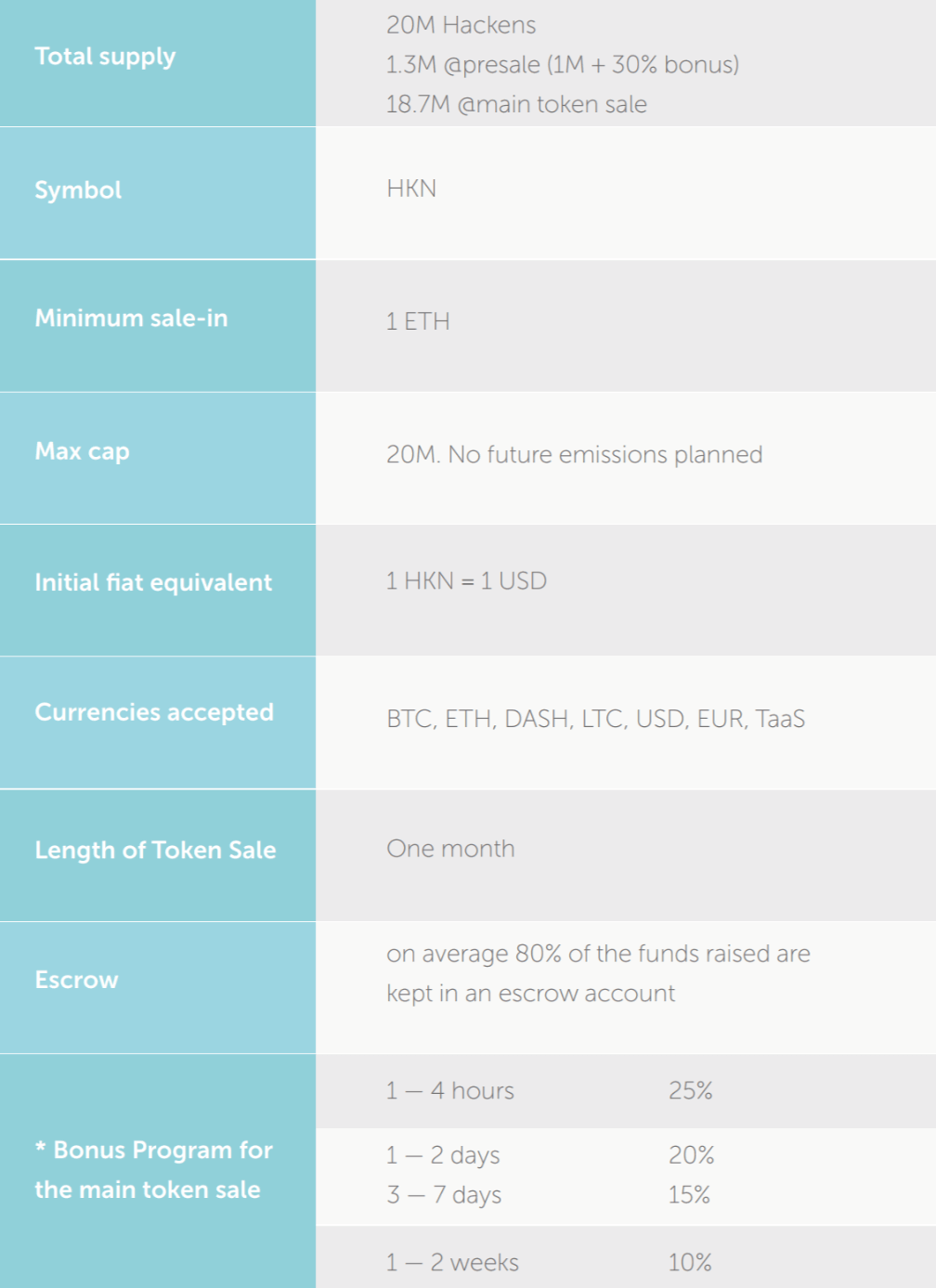 There’s a total of 20 million HKN that is fixed in supply and premined, with 14.96 million HKNs available for the token sale as 1.3 million HKNs are reserved for the presale and 3.74 million is reserved for the team, advisors and bounty program.
There’s a total of 20 million HKN that is fixed in supply and premined, with 14.96 million HKNs available for the token sale as 1.3 million HKNs are reserved for the presale and 3.74 million is reserved for the team, advisors and bounty program.
Token Economics
This means that the hard cap for the actual crowd-sale amounts to 14.96 million, which is relatively lower than most ICOs in the current landscape. This makes HKNs very attractive since there’s a low supply of HKN tokens available. It's much easier for the token price to exponentially increase as the surging demand for HKNs, coupled with a low available supply, would create scarcity and therefore push prices upwards. That's why low capped ICOs are appealing to “flippers”, or those looking for short-term gains by selling their tokens when it reaches an exchange. (See more: Crypto Guide 101: Choosing The Best Cryptocurrency Exchange)
Burning Model
A burning mechanism entails reducing the overall supply of HKN by “burning” the coins, which would have the effect of increasing the value of HKNs as there are now lesser coins to satisfy the current demand. This means that HKN is a deflationary currency, providing an incentive for investors to hold their HKNS and ethical hackers to earn HKNs for the work they provid. Here’s how it will work:
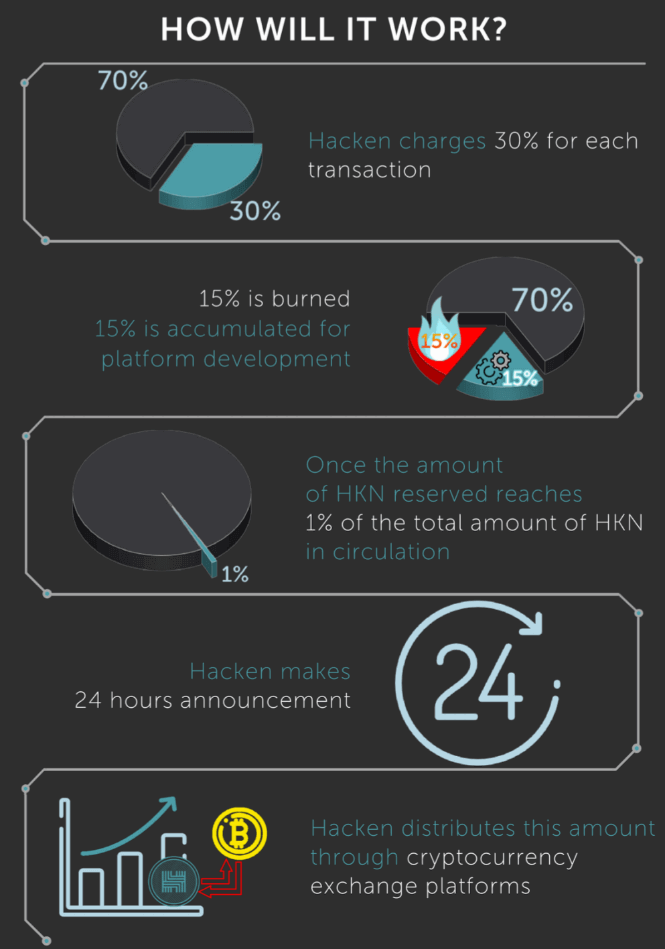
(Read also: Coins, Tokens & Altcoins: What’s the Difference?)
ICO Allocation
The allocation of HKNs are as follow:  The allocation of funds seem conservative, with 80% going to the development of the marketplace and 17% allocated to the team and advisors.
The allocation of funds seem conservative, with 80% going to the development of the marketplace and 17% allocated to the team and advisors.
Team
The Hacken team constitutes a list of experienced and capable individuals, with some serious credentials within the cybersecurity field. They also have academics – in the form of Dr Yegor and Dr Moe– who have authored 22 scientific papers in the field. It is also notable that the CFO (Budorin) and Community Director (Nikita) have close ties with Ukraine’s government administration, which could prove beneficial from a regulatory and credibility perspective. Hacken has recently announced that John Mcafee – the tech genius behind the antivirus software McAfee – will be an advisor to the project. This is a huge credibility boost given Mcafee's experience and stature in the cybersecurity sphere.
Traction
Awards: Hacken won 2nd place in the d10e ICO Pitch Challenge, a leading conference on Blockchain and ICOs. Hacken outmuscled hundreds of projects and was selected by the Blockchain Investors Consortium (BIC) as the runners-up. (See more: Beginner’s Guide to ICO Investing: How to Participate in ICOs)
Partnership: Hacken has unveiled a partnership with TAAS on October 13, the first-ever tokenized closed-end fund dedicated to blockchain assets. TAAS became the first institutional contributor to the Hacken ecosystem.
Strategic Cooperation: Hacken has recently announced a cooperation with Confideal, a platform for the creation, management and enforcement of smart contracts.
Roadmap
Here’s the scheduled roadmap derived from their whitepaper:
- HackenProof Marketplace — Q4 2017
- Analytics Center —Q1 2018
- Hacken Accelerator — Q4 2017
- Zero-day Platform — Q3 2018
- HackIT Conference — Q3 2018, new competitions and speaking panels at HackIT 2018 will be supported by Hacken
Strengths
- First Movers Advantage: The main competitors of Hacken are traditional penetration test firms that don't leverage the efficiency and network effect of Blockchain. This creates a strong competitive edge for Hacken
- Low Regulatory/Legal Risks: HKNs do not pay out any dividends. Instead, it integrates a burning mechanism that would reduce its overall supply and therefore increase the value of the HKN tokens. This, therefore, provides investors with price appreciation, and an incentive that doesn’t carry any regulatory weight (Dividend paying coins faces a huge risk of regulation as it is similar to a stock. Read more here: Crypto ICO vs. Stock IPO: What’s the Difference?)
- Credible Security Stamp: The credibility of Hacken largely depends on the effectiveness and quality of the Hacken community; the more (and better) ethical hackers it attracts, the greater its credibility as a cybersecurity platform. The potential for Hacken to attract ethical hackers through its Unreported Zero-Day Remuneration Fund and increasing store of value currency makes it much easier to leverage on the network effect, and the internal competition to solve bug bounty programs with efficiency would also contribute to the overall quality. This could very well result in a “stamp of approval” that is a mainstay in the industry
- Unreported Zero-Day Remuneration Fund: An extremely important feature that personifies the ethos Hacken stands for. Having a fund to reward undisclosed bugs ensures that the vulnerabilities are in the right hands and can be rectified in a transparent and accountable manner. Rather than rely on regulatory agencies, Hacken aims to create an effective digital discovery and evidence gathering mechanism to tackle the issue
- Strong Incentives for Investors: The combination of a relatively low-capped ICO with the mechanism of burning would diminish the supply of HKNs, which would increase the value of HKN for investors. Additionally, this creates an incentive for long-term holding, since the burning mechanism would kick in per the burning schedule
- Fostering Young Talent: The competitions within the annual conference serves as a great platform for Hacken to identify and develop young talent into ethical hackers. This is like killing two birds with one stone; it reinforces Hacken’s community-mindedness and would simultaneously strengthen the Hacken ecosystem
Summary
Overall, Hacken seems to be a very promising project, as it's a first mover into the cybersecurity field utilizing blockchain. More importantly, its objectives of proliferating ethical hacking and its development through solving a real business need (security testing and fixes) represents a natural fit. The success of Hacken’s ecosystem could set it up to be an authority in the cybersecurity arena, both in the traditional and blockchain industry.
Verdict: Excellent Project
Their ICO documentation can be found here.
Read also: A Guide To Fundamental Analysis For Cryptocurrencies
This represents the writer’s personal opinions and does not – in any way- constitute a recommendation of an investment or financial advice. Please assume caution when investing in cryptocurrencies and do so at your own risk, as it is extremely volatile and you can lose your money.
Get our exclusive e-book which will guide you on the step-by-step process to get started with making money via Cryptocurrency investments!
You can also join our Facebook group at Master The Crypto: Advanced Cryptocurrency Knowledge to ask any questions regarding cryptos!

I'm Aziz, a seasoned cryptocurrency trader who's really passionate about 2 things; #1) the awesome-revolutionary blockchain technology underlying crypto and #2) helping make bitcoin great ‘again'!




